Getting Started with Harbor

Recently I’ve gotten extremely excited by a newer CNCF project from VMWare called Harbor. Harbor is a powerful Docker and Helm registry that is simple to run inside Kubernetes. In this post we’re going to briefly go over what you need to deploy Harbor and some of the features that make it worth looking at.
Harbor is the combination of a few different services to build the actual registry. Harbor uses a customized version of the docker registry, Clair, Notary, and ChartMuseum. These come together ontop of the Helm UI to provide a very developer friendly experience. Helm is also multi-tenant friendly and can be integrated with an external user source, including OpenID Connect. If you’re using a service like Keycloak, Harbor is an amazing extension to have.
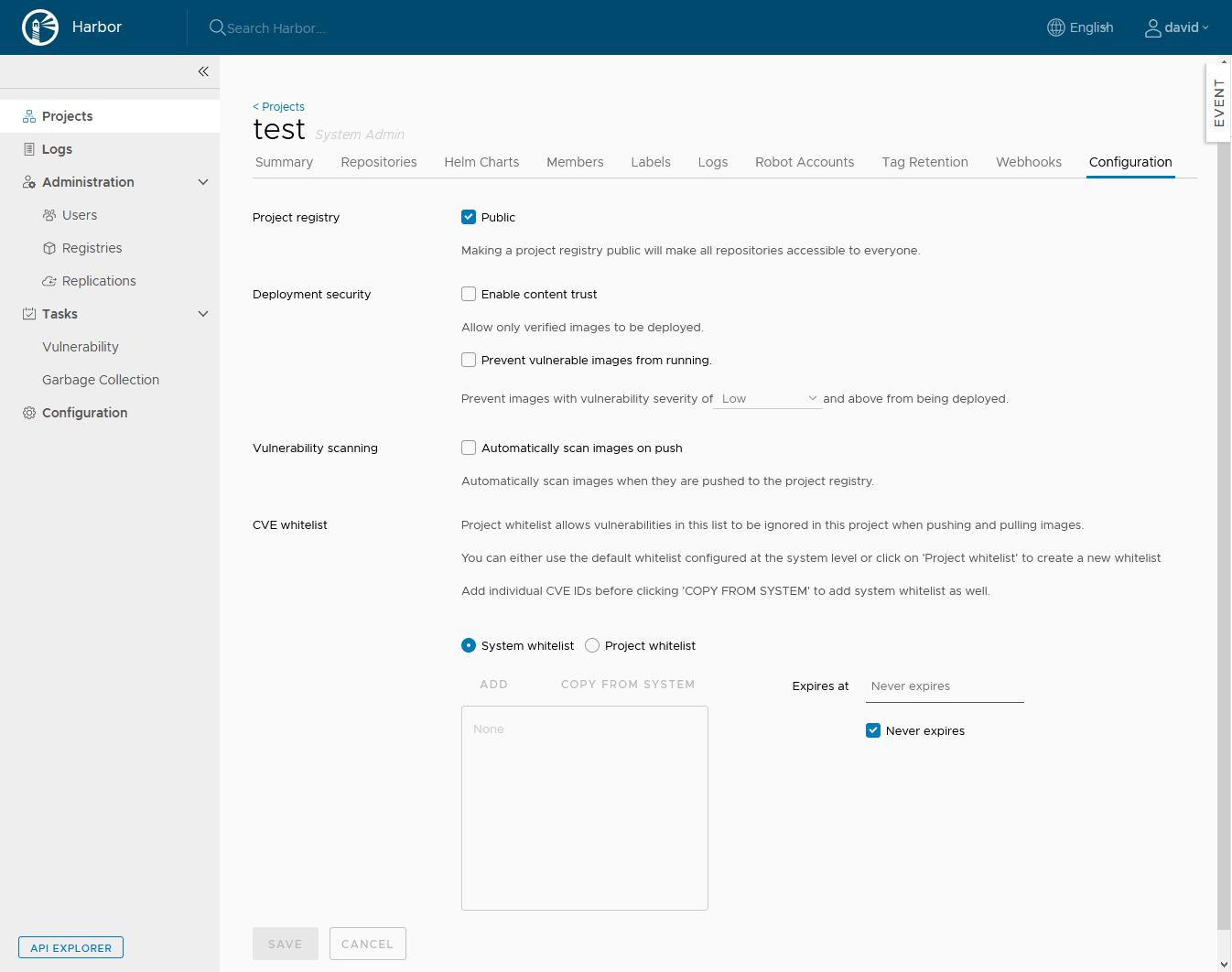
Harbor also has the ability to use Clair to do static vulnerability scans of your container layers and you can use notary to sign your images. Also at the project level you can set if Harbor will even allow unsigned or vulnerable containers from being served from Harbor. This is great for any environment, but is required if you have a compliant environment. The simplicity that Harbor brings to enabling these features make it worth a least a quick demo.
Luckily a demo is pretty easy to setup if you already have Kubernetes and Helm deployed. You can get the helm chart at https://github.com/goharbor/harbor-helm and they’re really good about keeping it up to date with the harbor releases. They version lock the Harbor release inside of the Helm release so you don’t end up with mismatched containers. The side effect of this though is you need to make sure to pull the latest copy of the helm chart before deploying as they do make changes between even minor verions inside the Helm chart.
Helm doesn’t require persistent storage, but to make it effective you really do need to have a way to present it. You will also need to provide some separate storage for the actual images. Harbor supports the local filesystem (which can then be pulled off into a PV), S3 (or S3 compatible), swift, Azure blobs, GCS, and OSS.
Once you have the values set, deploy the chart like normal and depending on your cluster’s auto-provision abilities you should then have a fully working endpoint you can hit. As of Harbor 1.9.2 the default username and password are admin and Harbor12345. You can also specify a password in the chart. Make sure to login, make a new account, then delete this default admin account.
Once you have done that you can start using Harbor right away. Create a new project and begin uploading new images. The configuration page for a Harbor Project
As long as all pods are running successfully Harbor should work without any concern. If you are running into problems though the most important containers are the harbor-core and registry pods. Check the logs there.
I hope that you get a chance to look Harbor over. It’s one of the less known CNCF projects that may really be able to turn around your image maintenance. I certainly have not covered all the features of Harbor either such as regional-replication. Have fun!